In today's digital landscape, ensuring the security and compliance of cloud-based projects is of paramount importance. Google Cloud Platform (GCP) offers a comprehensive suite of security features and compliance certifications to help protect our applications and data. In this blog, we will explore the key security and compliance considerations for college projects on GCP and discuss best practices to enhance security and meet regulatory requirements.
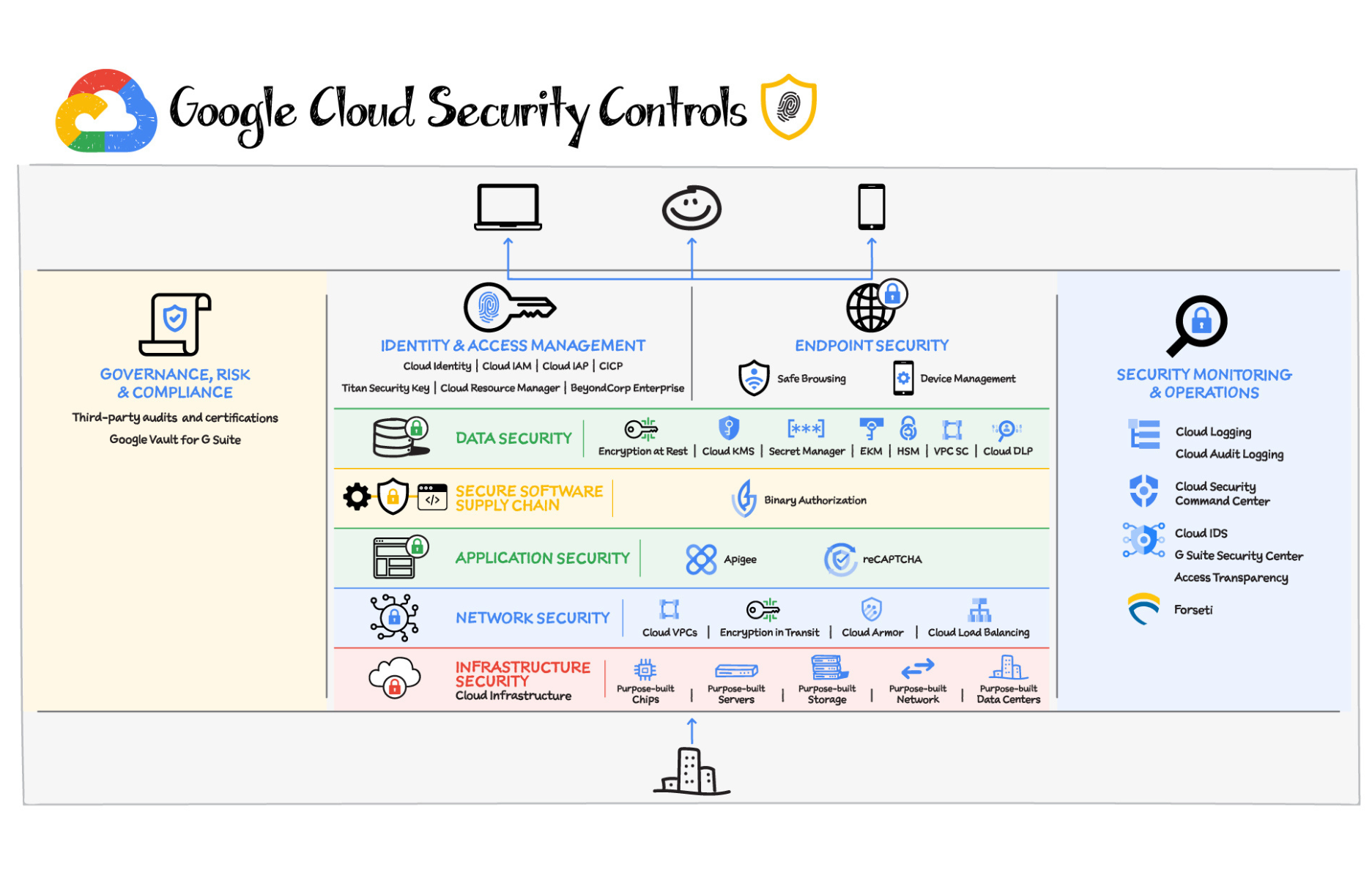
Understanding GCP Security Features
Google Cloud Platform provides a robust set of security features that can be leveraged to protect our college projects. These features include:
- Identity and Access Management (IAM): IAM allows you to manage user access and control permissions for GCP resources, ensuring that only authorized individuals can access sensitive data or make changes.
- Encryption: GCP offers various encryption options to protect data at rest and in transit. This includes default encryption for storage services, Key Management Service (KMS) for managing encryption keys, and SSL/TLS encryption for network communication.
- Logging and Monitoring: GCP provides logging and monitoring services, such as Cloud Logging and Cloud Monitoring, which enable you to track and analyze activity logs, monitor resource usage, and detect suspicious behavior.
Implementing Secure Networking
Networking is a critical aspect of securing our GCP projects. Consider the following best practices:
- Virtual Private Cloud (VPC): Set up VPCs with private IP ranges to create isolated environments for our projects. Configure firewall rules to control inbound and outbound traffic.
- Cloud Load Balancing: Utilize Cloud Load Balancing to distribute traffic and mitigate distributed denial-of-service (DDoS) attacks, ensuring high availability and scalability for our applications.
- Cloud CDN: Enable Cloud CDN to cache content closer to our users, reducing latency and improving performance while also providing an additional layer of protection against malicious traffic.
Managing Access Control and Permissions
Proper access control is crucial to protect sensitive data and prevent unauthorized access. Consider these recommendations:
- Principle of Least Privilege: Apply the principle of least privilege by granting users and services only the necessary permissions required to perform their tasks. Regularly review and update access permissions.
- Multi-Factor Authentication (MFA): Enable MFA for user accounts to add an extra layer of security, requiring an additional verification step, such as a code sent to a mobile device.
- Service Accounts: Utilize service accounts to manage authentication for applications and services running on GCP. Limit their permissions to reduce the potential impact of compromised credentials.
In conclusion, securing our college projects on Google Cloud Platform is essential to protect our data, ensure compliance, and build trust among our users. By leveraging GCP's robust security features, implementing secure networking, managing access control, and meeting compliance requirements, you can enhance the security posture of our projects. Embrace these best practices, and take advantage of GCP's comprehensive security offerings to safeguard our cloud-based applications.